Let's Defend: PHP-CGI (CVE-2024-4577)
Challenge Link: https://app.letsdefend.io/challenge/php-cgi-CVE-2024-4577
Scenario:
1
You will confront an attempted exploitation of a newly discovered and unpatched vulnerability (CVE-2024-XXXX) in a critical software component within your organization's infrastructure. The CVE allows for remote code execution, posing a significant threat if successfully exploited. At 12:05 PM UTC, an alert is generated by the Intrusion Detection System (IDS) and Intrusion Prevention System (IPS), indicating an attack on one of your web servers. Your task is to analyze the provided artifacts, confirm the exploitation attempt, and answer the provided questions.
File Location: C:\Users\LetsDefend\Desktop\ChallengeFile\artifacts.7z
Question 1
What version of PHP was running on the server during the incident?
To start, I was given a zip file that contained three folders:
- Apache24
- php
- Prefetch
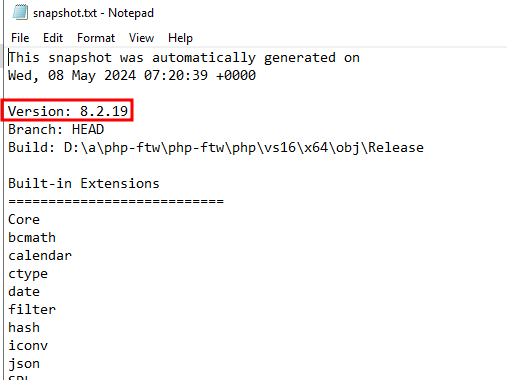
Considering the nature of the question, I investigated the php folder first. I scanned through all the files and snapshot.txt caught my eye. I opened it in Notepad and found a reference to the PHP version.
Answer:
8.2.19
Question 2
When PHP is configured to run as CGI, which directive in httpd.conf specifies the scripts that handle requests for PHP files?
In Apache24 > conf I found a file called httpd.conf
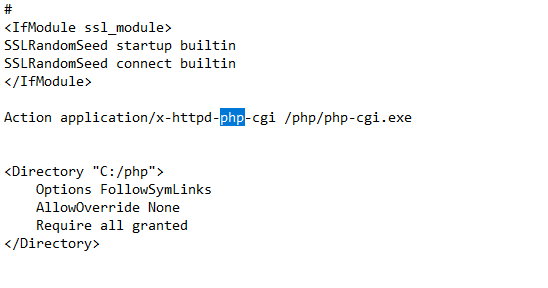
I then searched through the file with CTRL+F for the keyword “PHP” and found a few references to it. The one that looked most promising was this line at the bottom of the file: Action application/x-httpd-php-cgi /php/php-cgi.exe
Answer:
Action
Question 3
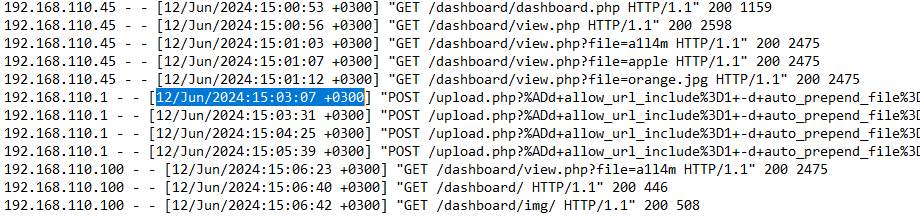
What is the IP address of the attacker who attempted to exploit our server?
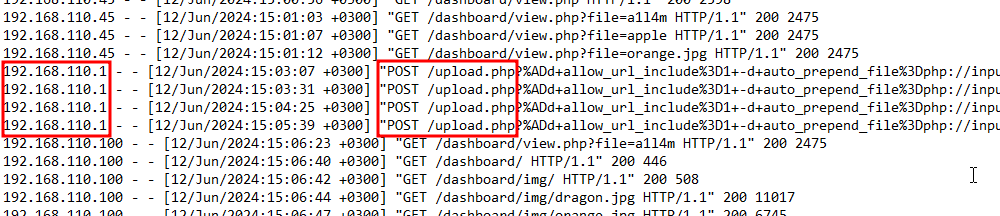
I then looked at the server’s access log found at Apache24 > logs > access.log. It appears the only IP address to attempt a POST request to the /upload.php so I was pretty sure this was it.
Answer:
192.168.110.1
Question 4
The attacker targeted a specific page on the server with malicious payloads. Which page did the attacker target with malicious payloads?
I already discovered the answer to this in the previous question.
Answer:
upload.php
Question 5
What version of Apache is running on the server?
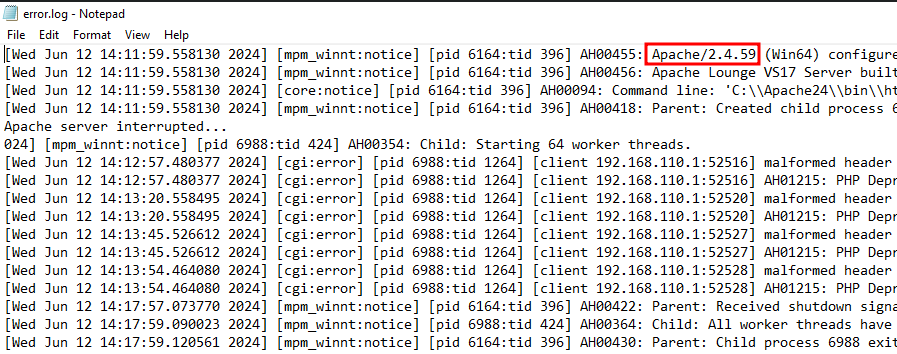
In the same directory as the access.log I had another file called error.log. On the first line of this file I found a reference to Apache’s version number.
Answer:
2.4.59
Question 6
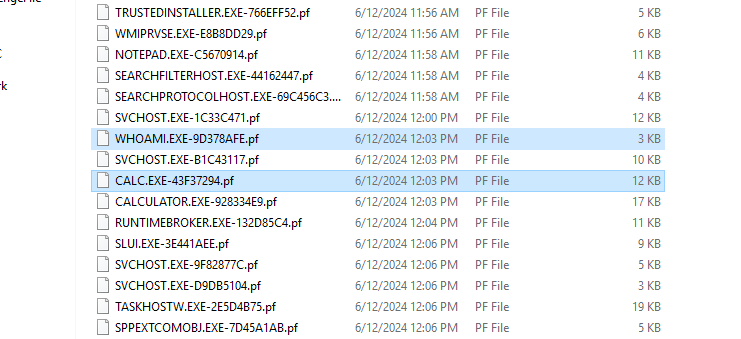
The attacker managed to execute commands on the server. What was the first process initiated by the attacker’s commands during their successful attempt?
For this question I had to look around a bit. I looked through files in the Prefetch folder but nothing particularly stuck out. I did notice each file had a different date modified time. I then took a look at the two Apache logs to see if there were any interesting times noted in the logs. Then I noticed the second attempt to POST /upload.php happened at 12/Jun/2024:15:03:07 +0300 and if you subtract 3 from the time to account for the timezone you get June 12th 2024 12:03pm.
I then checked this time frame out in the Prefetch folder and found something interesting:
Answer:
whoami.exe
Question 7
Before the attacker was detected and blocked, they executed another command, launching a new process. What process was launched by this command?
In the same screenshot above, just after launching whoami.exe the attacker launched calc.exe
Answer:
calc.exe
Question 8
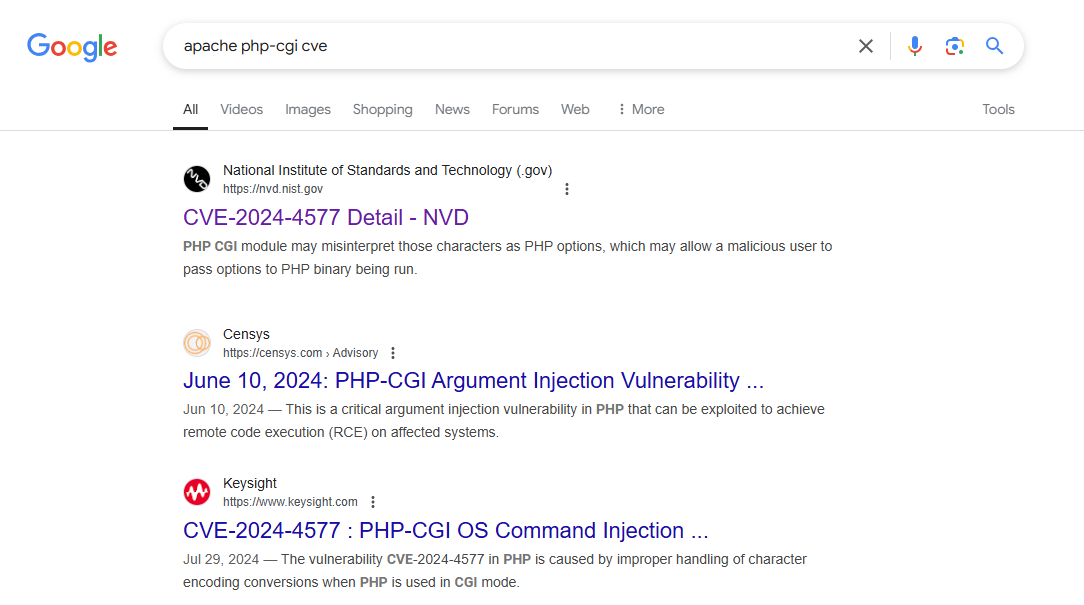
What is the CVE number of the exploit used by the attacker?
For this I had to think a little bit about what the attacker was trying to accomplish. They were attempting to abuse php-cgi on this Apache server. I searched these terms as well as the keyword “cve” and found a few immediate results for CVE-2024-4577.
Answer:
CVE-2024-4577