Let's Defend: Presentation As a Malware
Challenge Link: https://app.letsdefend.io/challenge/Presentation-As-a-Malware File link: /root/Desktop/ChallengeFiles/PO00187.zip Password: infected
Question 1
What was the general name / category of the malicious file in the analyzed ppt file?
Once I unzipped the file I uploaded the suspicious .ppt file to VirusTotal. Under the Detection tab it seemed basically all vendors flagged this as a Visual Basic Trojan Malware.
Answer:
VB:Trojan
Question 2
Which of the URL addresses it communicates with has been detected as harmful by sandboxes?
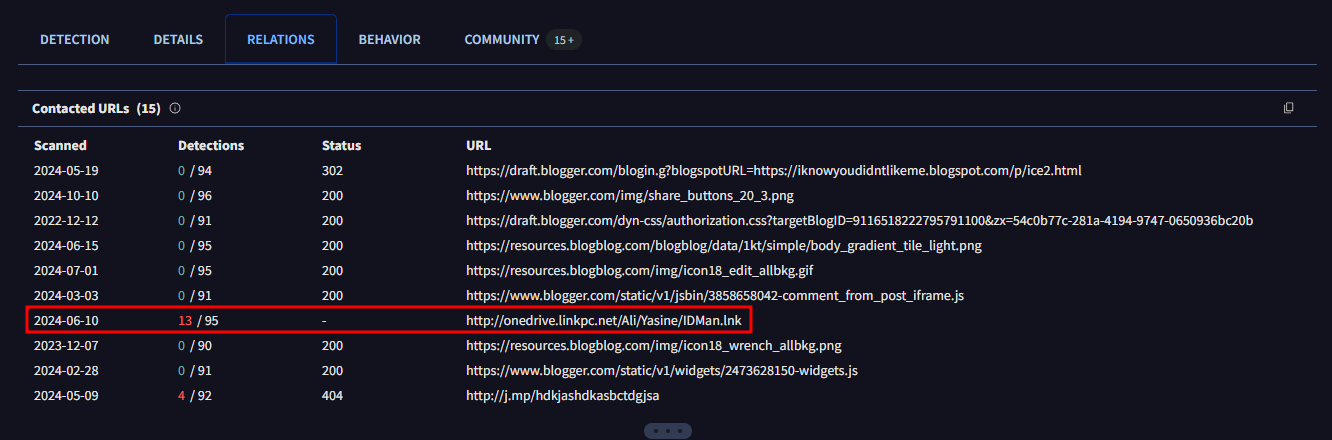
Under the Relations tab I found several Contacted URLs. The one that stuck out to me was highlighted in red with 13 detections.
Answer:
http://onedrive.linkpc.net/ali/yasine/idman.lnk
Question 3
What is the name of the htm file that drops to disk?
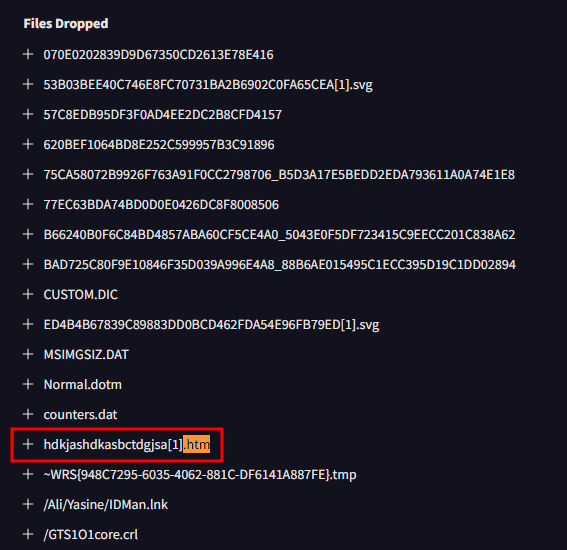
Next I opened the Behavior tab and used CTRL+F to search for the keyword “.htm” and looked for the result under the Files Dropped header.
Answer:
hdkjashdkasbctdgjsa[1].htm
Question 4
Which process is running to persistent under mshta.exe after the relevant malware runs?
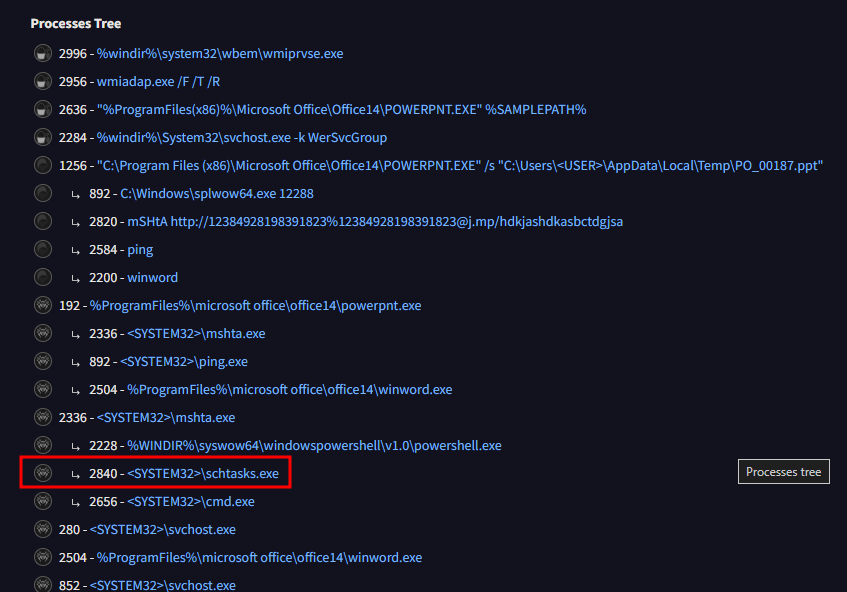
To find the processes running under mshta.exe I would need to visit the Processes Tree section of the Behavior tab results. Here I found three processes under mshta.exe:
- powershell.exe
- schtasks.exe
- cmd.exe
Since the question is asking about persistence, it is likely the schtasks.exe is the one I need since it can be used to create persistence by executing code on a set frequency.
Answer:
schtasks.exe
Question 5
If there was a snort IDS in the environment at the time of the incident, which rules would it match?
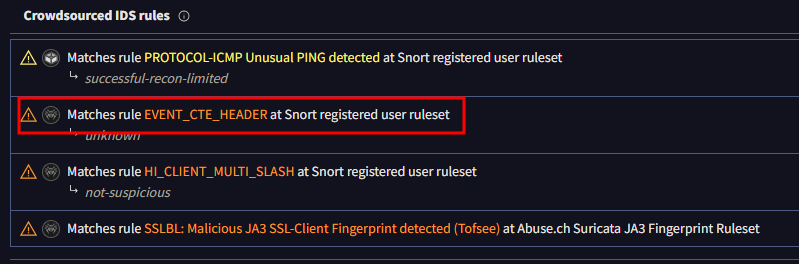
Further up on the page in the results was a section called Crowdsourced IDS rules. In it was a suggested Snort rule to catch this threat.
Answer:
EVENT_CTE_HEADER